Forked Futures
How Market Logic Locked the Internet Inside a Closed Circuit
Executive Summary
This essay conducts a forensic reconstruction of the brief window, 1997-2001, when the internet still promised broad-based mobility, tracing how a sequence of mutually reinforcing decisions (anti-poaching wage pacts, visa-enabled labor arbitrage, the suppression of nascent tech guilds, the enclosure of open code and user data, venture capital’s blitz-scale financing logic, and surveillance-funded revenue models) systematically narrowed that promise into a path-dependent regime of monopoly control.
Juxtaposing counterfactual “imagined paths” against the historical record, the essay demonstrates that each pivot point had a technically feasible alternative oriented toward distributed prosperity, yet capital’s incentives repeatedly selected for structures that depress wages, fragment labor solidarity, and convert behavioural exhaust into proprietary asset moats. The 2008 crisis then served as a consolidation catalyst, allowing cash-rich platforms to absorb competitors and install precarious gig labor as a normalized norm. The resulting behavioral casino now governs civic discourse, rendering traditional remedies (e.g., antitrust, labor law, privacy regulation) structurally inadequate because network saturation, switching-cost inertia, and regulatory capture lock the lattice in place.
The essay concludes that what remains is an obligation to understand the loss with empirical precision lest the historical record itself be subsumed by the systems that entombed the emancipatory internet alive.
I. Preface
Every system has a prime directive, and capital’s is clear: convert bargaining power into rent that compounds. It does this by seeking and closing every open seam in law, market structure, and social convention until value extraction becomes friction-less. The cheapest seam to close in any era is the one least defended, so capital’s first lever is always enclosure of something still common: labor mobility when human expertise is fluid, source code when software is shareware, data when clicks outnumber contracts. Once a seam is claimed, the cost of reversal rises exponentially because each successful enclosure finances the next.
This essay tracks those irreversible turns. At every historical fork a plural future remained technically possible, politically plausible, and, for a moment, publicly debated. Yet incentives pointed consistently toward the branch that deepened enclosure and multiplied rents. I recount each fork twice: first as the imagined path that engineers, policymakers, or workers could see at the time, then as the actual path capital chose. A personal witness interlude follows, anchoring the structural shift in one dated artifact and one hard number. The pattern repeats until no open seam remains, and the web, the workplace, and the polity converge into a closed circuit that serves the rentier first and the user last.
Read the sequence as a map; if the story feels obvious, that is precisely the warning it carries: every lock was visible before it snapped shut, and still the snap came.
II. The Moment of Promise and Method
The late 1990s were a brief intermission between two industrial epochs. Ethernet cable coiled across dorm-room floors, garage workbenches hosted improvised server racks, and ordinary retail space in Santa Clara became temporary command centres for fledgling dotcoms. Capital flowed through initial public offerings at valuations unanchored to reality, yet the most immediate engine of growth was human rather than financial. Technical vendor certifications (e.g., Certified Novell Engineer, Cisco Certified Network Associate, Microsoft Certified Systems Engineer, etc.) functioned as standardized professional passports. They converted raw aptitude and modest tuition into contract rates that rivalled mid-career salaries in legacy firms.
I entered that market with no lineage, a misaligned degree, and a starting wage of nineteen dollars/hr. Over six years, I accumulated forty-five technical vendor certifications, each one a discrete unit of legitimacy in an ecosystem feverish for accredited labor. By 2000, a single billable hour of my work commanded one hundred and seventy-five dollars. The leap was not extraordinary for the period; it was simply the yield available to anyone who could sprint through the open gateway before it closed. That rise, simultaneous with euphoric headlines about infinite demand for “web talent,” forms the empirical anchor of this essay.
The gateway closed quickly. Beginning in 2001, but rooted in structural shifts already underway, wage mobility narrowed, lateral hiring slowed, and certification premiums decayed. The lived trajectory recorded above therefore demarcates a vanishing aperture rather than a replicable path. This essay interrogates the mechanisms that widened and then sealed that opening, and in doing so reconstructs the delta between a plausibly emancipatory internet economy and the enclosure that followed.
The analytic method is tripartite. Each subsequent section offers: (1) an Imagined Path, the practitioner-centric counterfactual that was technically and politically viable at the time; (2) the Actual Path, the sequence of policy, capital, and firm-level decisions that produced professional enclosure; and (3) a Witness Interlude, a concise empirical vignette drawn from the author’s experience that establishes the phenomenon’s lived veracity. The three strands are presented in parity to prevent moral nostalgia or deterministic fatalism from displacing evidence.
A brief connective paragraph concludes every section, demonstrating how the divergence just analyzed becomes causal substrate for the next. In this way the essay moves sequentially from open labor markets to immigration policy, guild formation, code ownership, capital structure, social architecture, macroeconomic shock, present-day monopoly, and finally the ledger of irrevocable losses. No remedial program is offered; none exists within the logic that consolidated after the gateway shut. The aim here is to provide an exact description of forces at this confluence of business, civic, and political history.
III. Labor Market Dynamics: Free Agency vs Wage Cartel
Imagined Path: An Engineer’s Free-Agency Market
In the counterfactual trajectory, technical labor would have evolved along lines already visible by 1998. Recruiters openly compared offers, managers engaged in week-long bidding wars, and early web forums published granular compensation surveys. Under such conditions, software engineers resembled professional athletes: portable franchises of expertise, equipped with representation, poised to renegotiate whenever a competitor expressed interest. Salary transparency served as a practical necessity: teams could not risk lowballing when rival firms were prepared to escalate on the public record.
The economic logic of this environment discourages hoarding. Retention is secured through working conditions, intellectual autonomy, and immediate cash premiums rather than deferred equity. High turnover is tolerated because the replenishment pipeline (boot camps, vendor academies, community colleges) remains robust and well-funded. In this world, the median engineer’s wage approximates the marginal revenue product of code rather than the concessionary outcome of structural bargaining imbalance.
Actual Path: The Quiet Construction of a Wage Cartel
The real economy inverted that logic. Between 2005 and 2007, executives at Apple, Google, Intel, Adobe, and others formalized non-solicitation pacts that had been informally practiced for a decade, as later revealed in U.S. Department of Justice filings. These agreements, combined with region-specific non-compete clauses and mandatory arbitration policies, froze lateral mobility precisely where bidding should have intensified. Concurrently, the industry shifted compensation weight from immediate salary to restricted stock units on four-year cliffs. Equity, marketed as upside participation, became a timed shackle: walking away meant forfeiting unvested tranches.
By suppressing visible wage competition, firms flattened the compensation curve for mid-career technologists. Entry salaries remained superficially strong (maintaining the narrative of boundless demand), yet longitudinal data showed stagnation. The “average Google engineer” no longer earned more each year because of bidding pressure; she earned more only if the share price obliged. The practitioner’s upside had been transformed from negotiated price to speculative equity, and speculation is structurally indifferent to the individual.
Witness Interlude
During the window from 1997 to 2000, a dual CCNA/MCSE skillset routinely commanded six-figure contract rates for short-term infrastructure builds. I signed three-month engagements at $175/hr, turned down counteroffers, and expected the next recruiter call within days. In 2006, possessing identical certifications and deeper experience, I fielded full-time offers that converted to roughly $55/hr when equity risk was discounted: a nominal raise over my original help-desk wage if adjusted for inflation, but a precipitous decline from the free-agency apex. The cartel’s effects were line-items on my offer letters.
Once wage ceilings hardened, firms sought alternative cost arbitrage. The suppressed domestic market created structural demand for less expensive, more pliable labor streams, chief among them the H-1B visa pipeline. Thus, labor cartelization did not merely coexist with immigration-based substitution; it generated the appetite that would define the next stage of enclosure.
IV. Immigration Policy: High-Skill Exchange vs Wage Arbitrage
Imagined Path: Selective Mobility as National Capacity-Building
Had policy makers treated the H-1B statute as a surgical instrument rather than a volume discount, the visa would have enforced scarcity and reciprocity. Annual caps would have remained well below market demand; employers would have been compelled to prove not merely unavailability of domestic labor but failure of demonstrable apprenticeship efforts. Prevailing-wage audits, benchmarked to the ninetieth percentile, would have neutralized price arbitrage and aligned foreign compensation with the bidding wars described in the prior section.
In parallel, every approved petition would have triggered a proportional contribution to regional training funds. Those funds, distributed through community colleges and vendor academies, would have seeded new hubs in St. Louis, Cleveland, Albuquerque, locations where the cost structure could support both firm profitability and middle-class wages. In this counterfactual, immigration functions as a high-skill exchange, enriching both the entrant and the domestic base rather than displacing the latter.
Actual Path: Visa as Commodity and Wedge
The legislative reality evolved in the opposite direction. Caps were periodically lifted or circumvented through consulting-company exemptions; enforcement budgets remained static; prevailing-wage calculations relied on coarse occupational categories that allowed systematic understatement. Specialized “body-shopping” firms surfaced to sponsor thousands of candidates, bench them at sub-contract rates, and redeploy them across client sites with little oversight.
For employers, the mechanism offered two advantages: labor at a thirty-to-forty-percent discount and an employee coercively bound by visa dependency. For incumbent domestic workers, the effect was less substitution than deterrence. Teams witnessing mid-contract replacement internalized the new ceiling on wages and leverage. Meanwhile, workplace solidarity fractured along lines of origin, tenure, and visa status, replacing nascent guild consciousness with silent competition for the remaining high-trust roles.
Witness Interlude
My first large-scale rollout (1999) fielded an infrastructure team drawn entirely from metropolitan labor pools; the onboarding of a new cohort meant a collective pay-raise expectation. By 2006, during a follow-up contract at the same client, the entire quality-assurance wing was replaced in a single quarter by visa-dependent staff billed through a third-party vendor. The cost savings were explicit: the project manager cited a fifty-five-percent reduction via arbitrage. For the incoming class of local graduates, the entry ladder had been removed. For those of us already ascended, bargaining power turned symbolic: technical credentials mattered only insofar as they justified the rate differential capital was now determined to erase.
Workplace segmentation (citizen versus non-citizen, direct hire versus vendor bench) dissolved the conditions necessary for collective wage action. The guild impulse that might have countered the wage cartel foundered on a labor force now engineered for disunity.
V. Collective Power: Early Tech Guilds vs Perpetual Atomization
Imagined Path: Guilds, Ethics, and the Prospect of Industrial Citizenship
Had labor’s trajectory remained aligned with its late-1990s velocity, software professionals would have crossed the threshold from occupation to craft jurisdiction by 2001. Preliminary signs were present: Bay Area “coder councils,” NYC Linux user-group legal clinics, and dot-org campaigns to standardize rates for contract labor. A formal guild would have operationalized those prototypes, asserting jurisdiction over skills accreditation (mirroring medical boards), enforcing collectively bargained floor rates, and most critically, embedding ethical veto power in its charter.
Such a body could have framed a refusal doctrine against emergent state surveillance after September 11, 2001. The leverage would rest on the credible threat of a concerted work stoppage across interdependent firms. Absent rapid compliance with guild standards (transparent bidding, humane hours, privacy-respecting architectures), key talent would simply walk, halting product roadmaps at scale. Comparable leverage existed in the International Typographical Union and the Screen Actors Guild at analogous stages of industrial consolidation.
Actual Path: Individualized Loyalty Economics
Corporate strategy neutralized these embryonic structures via a two-pronged attack: atomization of employment contracts and pre-emptive capture of worker identity. Non-compete clauses, once restricted to C-suite roles, cascaded down to ordinary developers. Mandatory arbitration silenced collective grievances. Share-option lotteries reframed loyalty as personal upside rather than class alignment. By the time “move fast and break things” became a mantra, the underlying labor settlement had already moved past collective voice to exit-or-silence as the only sanctioned responses.
Management added soft containment: free gourmet lunches, shuttle services, laundry drop-off, and campus wellness centres that blurred the spatial boundary between firm and worker. These perks cost less than a one-percent rise in base salaries yet re-encoded professional identity: the engineer became not a practitioner within a guild, but a citizen of the corporate polis, her grievances folded into an HR feedback loop optimized for retention analytics.
Witness Interlude
In 1999, I negotiated a fixed-scope contract with an explicit forty-hour ceiling; the client’s attempt to impose weekend overtime triggered a rate adjustment clause I had drafted myself. They conceded within forty-eight hours. A decade later, reviewing an employment agreement at a comparable firm, I encountered a mandatory arbitration section, a broad confidentiality rider, and a non-compete binding me for twelve months; non-negotiable, according to HR. The attorney who vetted the offer confirmed these provisions had become “industry standard.” My leverage, once predicated on scarcity of skills, evaporated under structurally flattening of contracts.
Without a guild’s collective firewall, the defence of open technical standards defaulted to volunteerism. Fragmented labor lacking institutional power could not resist corporate appropriation of shared code or the translation of community protocols into proprietary APIs.
VI. Ownership of Code: Federated Commons vs Walled Gardens
Imagined Path: Protocol Sovereignty and Portable Identity
Had labor retained collective leverage, the licit successor to early internet infrastructure would have been a federated commons. The building blocks already existed: the Apache stack as reference web server, Mozilla’s Gecko engine as browser backbone, Gnutella’s peer-to-peer schema for file routing, and RSS for publish-subscribe distribution. In that historical trajectory, commercial vendors would have competed on implementation quality (security, latency, interface polish) while preserving wire-level compatibility. A user could shift from one hosting service to another without data loss, as effortlessly as dialling a new long-distance carrier in 1985.
Under such conditions, social networks would have evolved as interoperable services rather than walled silos. Identity tokens signed by community guilds, storage delegated to commodity providers, and message routing negotiated by open protocols would collectively deny any single firm unilateral control over social graphs. Venture capital could still profit (integration consulting, hosted premium tiers, vertical applications) but it would do so inside a competitive terrain bounded by shared open standards. The commons would function as substrate; value capture would depend on differentiated service, not coercive possession of user data.
Actual Path: Enclosure of Commons and Creation of Moats
The reality inverted this logic. Venture-funded platforms adopted a bait-and-capture sequence: promote open-source collaboration to accelerate time-to-market, then relicense or API-gate the resulting functionality once network effects took hold. Facebook subsumed XMPP to proprietary chat extensions; Twitter throttled third-party clients after securing critical mass; Amazon’s fork-and-freeze of Elasticsearch converted community labor into a managed-service monopoly.
Data gravity completed the enclosure. Unlike traditional intellectual property, user-generated data is non-substitutable; the only canonical copy is the one held by the platform. Firms converted this asymmetry into a defensible moat: switching costs grew with every new interaction, every “like,” every uploaded image. Open-source licenses could not compel portability when the primary asset was no longer code but the behavioural exhaust locked behind authentication walls. Platforms thus extracted uncompensated surplus from both contributors (who wrote the code) and users (who produced the data), monetizing network effects that the commons had originally enabled.
Witness Interlude
In 1998, publishing patches to the Apache codebase via SourceForge translated directly into negotiating power: each accepted commit raised my billable rate, because clients could verify merit in public view. By 2012, the primary venue for contribution had migrated to GitHub, whose terms of service allowed the host to sublicense or commercially exploit repository content without additional consent. Some of my utilities shared under permissive licenses were packaged into proprietary SaaS offerings by firms whose only added value was branding and venture backing. My reputation still existed, but the rent now flowed elsewhere.
With the code commons enclosed and behavioural data sequestered, intellectual property ceased to be a cooperative substrate and became a private lever. Capital could dictate a single optimal growth model (blitz-scaling) in which speed of capture outweighed profitability, sustainability, or worker equity.
VII. Capital Structure: Cooperative Equity vs Blitz-Scaling
Imagined Path: Slow Money and Employee Governance
Had intellectual property remained in the commons, capital would have entered the sector as a facilitator rather than as sovereign owner. Firms, modest in headcount yet profitable from inception, could finance growth through retained earnings or credit priced on demonstrable cash flow. Boards structured on German-style codetermination or ESOP heavy allocations would institutionalize labor’s stake: employees holding a super-majority of voting shares while outside investors received non-voting preferred equity with capped returns.
Such architecture aligns incentives across time horizons. Liquidity events are optional, not existential; dividends substitute for 10× exits. Market share can stabilize below monopoly thresholds because value capture is derived from service quality, not network-effect rents. The opportunity cost of hyper-growth falls on capital, not labor, so decision calculus favors resilience: balanced books, transparent governance, cautious expansion into adjacent markets only when operational capacity warrants.
Actual Path: Blitz-Scaling as Capital’s Dominant Logic
Once code and data moats emerged, venture capital pivoted from patient patron to controlling architect. The optimal financing play became blitz-scale or die: raise successive rounds at geometric valuations, subsidize user acquisition until switching costs lock in, then lever monopoly power into advertising, fees, or margins. Term sheets embedded liquidation preferences and ratchets that guaranteed investors disproportionate claim on any eventual payout, even at modest exit prices.
For employees, the nominal lure was equity upside, but option grants sat beneath layers of dilution, secondary carve-outs, and waterfall clauses. Founders negotiated early partial liquidity (the “secondary share sale”) while rank-and-file engineers remained illiquid. Corporate governance formalized the asymmetry: dual class shares insulated executives from ordinary shareholders, and investor board seats outnumbered employee observers. Blitz-scaling thus produced a firm that could spend unprofitably for a decade, sustain negative externalities at scale, and still deliver 100× multiples to late-stage funds upon IPO.
Witness Interlude
In 1999, I joined a thirteen-person consultancy whose charter mandated a 50-percent profit share with engineers. Year-end distributions exceeded base salary, and strategic decisions required unanimous consent of employee-owners. In 2018, I held options in a well-known platform start-up. The share price required for my options to vest above strike rose each funding round. When the company eventually sold in a down-round, investors received their 1× liquidation preference plus accumulated dividends. My options, still unexercised, were bought out at discount. The rhetoric of shared upside masked a one-directional transfer of risk.
Blitz-scale economics demanded user counts that outran revenue. To satisfy investor growth curves, firms defaulted to “free” services subsidized by behavioural data and targeted advertising. Thus, capital’s governance logic seeded the surveillance-advertising complex that would shape the social architecture described next.
VIII. Social Architecture: Paid Utilities vs Ad-Fuelled Manipulation
Imagined Path: Utility Pricing and Data Modesty
In a commons-oriented ecosystem, communication software would have adopted the economics of other networked utilities: flat-rate or tiered subscription, transparent service metrics, and contractual data minimization. Identity and message storage would reside, encrypted, on servers chosen by the user or a cooperative; platform operators would possess, at most, custodial access. Revenue growth would track the slow arithmetic of new seats sold, not the geometric spirals of speculative valuation. Community moderation (e.g., elections for forum stewards, publicly logged policy changes) would embed governance within the user base, constraining profit motives with participatory oversight. The business model would resemble managed email circa 1997, scaled with modern bandwidth, rather than a casino for human attention.
Actual Path: Surveillance as Business Model
Blitz-scaling firms could not satisfy investor growth curves on subscription income, so they externalized price and internalized surveillance. The metric of health became monthly active users, not retained revenue. Product teams, armed with telemetry pipelines, A/B-tested interface tweaks that maximized session duration and emotional arousal. Algorithmic ranking optimized for engagement regardless of semantic value, generating outrage cycles that fed the ad auction with fresh impressions. Data retention defaulted to indefinite; privacy controls surfaced only when regulation loomed. Behavioural surplus (click cadence, dwell time, cursor velocity) became proprietary signal for predictive advertising markets. The platform thus monetized affective states while claiming the service was “free.”
Witness Interlude
In 1998, enterprise clients subscribed to GroupWise and Lotus Notes at roughly $18/seat per month, plus support. Architecture reviews focused on uptime and directory integration; data monetization was not a topic because none was contemplated. About a decade later, identical clients asked me to integrate apps containing third-party ad-tech SDKs that harvested device IDs and location pings. The subscription line item vanished; revenue now arrived as a rev-share on user exhaust sold through real-time bidding exchanges. The very concept of paying for software was reframed as naïve: “why charge when you can monetize engagement?”
Advertising surplus created cash reserves and credit lines unavailable to subscription-bound competitors. When the 2008 financial crisis struck, these reserves underwrote acquisition sprees and price wars that eliminated weaker firms. The surveillance-revenue cushion thus became the shock absorber, and weapon, of the consolidation examined in the next section.
IX. Macro Shock 2008: Resilient Pluralism vs Crisis Consolidation
Imagined Path: Distributed Shock Absorption
Had the internet economy remained a mosaic of midsize, cash-generating firms, the 2008 financial crisis would have resembled a hard winter rather than an extinction event. Profit-positive balance sheets could have financed payroll through the demand trough, while temporary pay-cuts or work-sharing schemes dispersed pain across payroll classes instead of eliminating headcount. Absent outsized platform dominance, laid-off specialists would have found lateral positions at peer companies rather than scrambling for contingency gigs. Concurrently, stimulus policy conceived as digital infrastructure might have seeded municipally owned broadband cooperatives and open-access fibre, lowering future entry barriers for new providers. The result: contraction, yes, but a sector that emerged leaner, still plural, and still grounded in norms of mutual obligation, adaptability, and cooperation.
Actual Path: Liquidity as Weapon and Wedge
In reality, the firms that had funded operations through surveillance advertising entered the crisis with war chests of cash and nearly unlimited access to revolving credit. As venture capital froze, distressed start-ups accepted fire-sale acquisitions; larger incumbents slashed R&D and marketing, effectively conceding market share to the platforms most capable of weathering zero-revenue intervals. The same capital logic that had demanded blitz-scaling now demanded asset scavenging.
Simultaneously, the recession mainstreamed gig labor. What began as supplemental income for over-credentialed under-employed workers became, by necessity, a primary wage channel. On-demand ride services and task platforms pitched “entrepreneurship” while shifting depreciation, insurance, and idle-time risk onto individual contractors. Precarity, once an exception in technical fields, was rebranded as flexibility and installed as a normative labor relation. Platforms deepened data extraction to optimize gig dispatch and dynamic pricing, turning real-time local labor markets into profit centres.
Witness Interlude
Before the crash, my contract slate extended nine months ahead; rates were indexed to scarce skill sets rather than macro cycles. By Q2 2009 every renewal evaporated within six weeks. Recruiter calls redirected me to platform-mediated piecework: project sprints, strategic rewrites, short-term infrastructure work posted on auction sites. Effective hourly compensation, net of fees, hovered at one-third my pre-crisis baseline. The platforms filled my calendar but emptied the profession of bargaining power.
Post-crisis consolidation locked in a new equilibrium: a handful of vertically integrated platforms controlling user identity, data exhaust, and labor allocation. The internet that emerged is behaviourally sculpted by monopolies whose operating logic derives from the consolidation moment; this structure governs digital life to this day.
X. Present Tense: Public Utility Internet vs Behavioural Casino
Imagined Path: Civic Infrastructure and Data Commons
Had post-crisis policy steered the sector toward public-utility principles, broadband carriage would now resemble electricity distribution: regulated rates, universal-service obligations, and structural separation between conduit and content. End-to-end encryption would be baseline and uncontested. Personal data would reside in fiduciary trusts governed by municipal or cooperative charters; services would request revocable access rather than permanent transfer. Interoperable identity standards analogous to SMTP for e-mail would let users port social graphs and reputations across providers without economic penalty. In this configuration, value accrues through reliability and civic trust, not attention arbitrage.
Actual Path: The Behavioural Casino
Instead, the consolidated platforms fortified their moats. Tracking pixels infest nearly every public website; cross-device identity graphs reconstruct behavioural patterns at minute resolution. Recommendation engines maximize engagement by accentuating novelty, outrage, or grievance, thereby generating ad inventory priced in programmatic auctions. API endpoints that once permitted third-party innovation now sit behind rent-seeking paywalls, prices calibrated not to recover cost but to suppress competitive entry. Legislative oversight is neutralized by revolving-door appointments and think-tank white papers authored, in effect, by lobbyists. Regulation that does pass often codifies the status quo: it raises compliance costs beyond the reach of upstarts while imposing only marginal constraints on incumbents.
The result is a behavioural casino layered atop critical infrastructure. Users spin the algorithmic wheel with every scroll; the house, armed with perfect telemetry, sets odds anew in real time. Collective discourse, once an emergent property of networked publics, is now a by-product of bid optimization.
Witness Interlude
In 1999, I maintained a website on a rented server: FTP uploads, raw HTML, a visitor log in plain text. Advertising, limited to a static banner, covered hosting fees and yielded perhaps fifty dollars a month in surplus: modest, predictable, transparent. Today, the same self-hosted content circulates only if embedded within a platform feed. Algorithmic curation suppresses posts lacking “engagement signals,” while revenue (fractional pennies per thousand impressions) flows through opaque dashboards subject to unilateral policy shifts. Control over distribution, monetization, and even archival permanence has migrated from author to platform without negotiation.
The present regime’s scale and adhesion illustrate path dependence. Network effects, data accumulation, and regulatory insulation have pushed the system past a threshold where conventional competition or incremental reform cannot unwind it. The next section formalizes these dynamics, quantifying the feedback loops and irreversibility conditions that now define the structure.
XI. Structural Analysis of Path Dependence
A. Capital–Labor Incentive Matrix
The foundational condition of enclosure is a skewed incentive matrix that aligns capital’s optimum with labor’s minimum. The anti-poaching agreements of Section II functioned as an exogenous shock that reset expected compensation downward. Once employers internalized wage suppression as a feasible equilibrium, subsequent hiring and budgeting models incorporated the lower baseline as a constant. The matrix therefore locked in a dominant strategy for capital (constrain mobility, externalize training costs, internalize surplus) while relegating labor to defensive moves: credential accumulation, lateral transfers, and equity gambles. Over multiple iterations, the Nash equilibrium converged on persistent wage stagnation, independent of individual productivity or scarcity.
B. Feedback Loops and Self-Reinforcement
Enclosure of code (Section V) and user data (Section VII) supplied the feedstock for a second-order loop:
Data Aggregation → Predictive Precision → Higher Ad Yield
Higher Ad Yield → Venture Liquidity → Acquisition Budget
Acquisition Budget → Larger User Base → Greater Data Aggregation
The loop amplifies both bargaining asymmetry and surveillance incentives. Each marginal user increases platform revenue non-linearly, funding still more extraction. Labor arbitrage persists because surplus does not return to wages; it finances growth designed to dilute worker leverage. The system thus approaches a runaway kinetic: velocity limited only by antitrust intervention, which has been constrained, in turn, by regulatory capture outlined in Section IX.
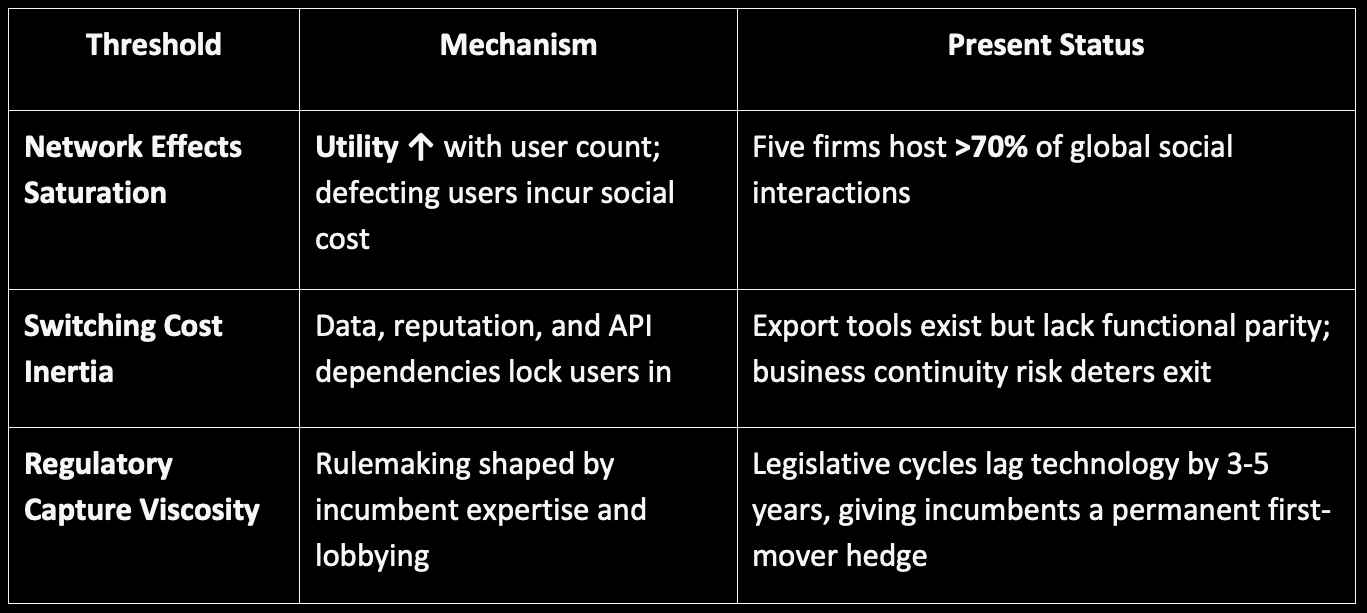
C. Irreversibility Thresholds
Classical remedies such as competition policy, labor law, and privacy regulation presume a market still capable of reconfiguration. Three thresholds indicate we have crossed beyond that presumption:
Collectively these thresholds produce a hysteresis effect: displacement forces must exceed not only the original enclosure impulse but the accumulated mass of the feedback loops. Absent an exogenous shock of state-level re-architecture or catastrophic platform failure, reversal is statistically negligible.
D. Witness Reflection
My own trajectory illustrates the lock-in. Between 2010 and 2022, I added cloud orchestration, container security, and ML-ops certifications to maintain relevance. Billable rates in constant dollars did not rise; in some cycles they declined. The marginal return on each new skill diminished as platform API abstractions embedded the functionality I once delivered. Human capital could not outrun a structure that valorizes control of data pipelines over mastery of tools. The matrix, once tilted, never resets.
XII. Societal Ledger of Lost Futures
A. Wealth Distribution: The Stalled Class Elevator
The counterfactual internet promised geographically diffused prosperity: midsize integrators in Salt Lake City, managed-hosting firms in Memphis, regional SaaS vendors in Halifax. Under enclosure, that uplift never materialised. Income gains concentrate in the narrow band of equity-eligible staff clustered around coastal headquarters, while non-founding engineers experience stagnant real wages. Platform shareholders extract supra-normal rents from data monopolies; downstream suppliers and contractors absorb margin compression. By 2025, the top decile of tech-sector earners captures a larger share of industry income than the bottom seven deciles combined, crystallising a barbell economy that mirrors gilded-age rail monopolies.
B. Democratic Agency: Governing at a Technological Deficit
Legislatures once set the operational perimeter for common carriers; today they follow, not lead. De facto rulemaking migrates to standards bodies controlled by incumbents who draft protocols first and present faits accomplis later. When statutory intervention does occur (e.g., GDPR, CCPA, DMA), the regulatory architecture is sufficiently complex that only incumbents possess the compliance scale to absorb it, further insulating them from competition. Campaign finance and revolving-door appointments tighten the loop: policy entrepreneurs with platform pedigrees occupy oversight posts, while committee hearings devolve into technical tutorials. The electorate, asked to adjudicate issues it cannot meaningfully audit, cedes agency by default.
C. Epistemic Stability: The Commons as Algorithmic Spoil
Public discourse once relied on editorial curation and shared temporal cadence. Platform ranking systems replace those filters with reactive engagement heuristics, atomising the informational substrate into context-free packets optimised for volatility. The cost of fabricating persuasive falsehoods approaches zero, while the cost of forensic rebuttal remains high and slow. Resultant epistemic drag impairs collective problem-solving from pandemic response to climate adaptation because a minimal consensus reality cannot be sustained. Where the imagined internet would have broadened analytic capacity via interoperable data trusts, the behavioural casino fragments it into monetizable micro-audiences.
D. Witness Reflection
Colleagues who attempted my 1990s certification sprint in 2012 earned CompTIA and AWS associate badges, only to accept entry-level help-desk roles at outsourced providers. Four years later, they remained on tier-one night rotations, their path to mid-career engineering blocked by wage ceilings and visa-mediated substitution. Certification still signals competence, but the ladder it once unlocked has been mechanically removed. Their stagnation is not an individual failure; it is structural foreclosure rendered visible at human scale.
XIII. Mourning, Memory, Leverage Points
This essay charts a single, widening divergence. At every inflection point (labor mobility, immigration design, guild formation, code ownership, capital structure, revenue model, macro-shock response), one path pointed toward distributed prosperity while the other cemented enclosure. Each fork was independently survivable; taken together, they congealed into a self-reinforcing lattice. By the time network-effect monopolies matured, the combinatorial lock had no remaining tumblers to turn. The internet’s emancipatory interval narrowed from possibility to anecdote, then to fossil.
The counterfactual arc we explored is therefore not speculative fiction but archival fact. A six-year slice of empirical evidence (contract rates, certification premiums, SourceForge reputational capital) demonstrates that alternative equilibria were momentarily operational. Those data invalidate the claim that enclosure was technologically inevitable or economically necessary. The personal witness thread anchors abstraction in lived materiality: what was viable for one cohort became impossible for the next because the structural doors were welded shut by its beneficiaries.
No remedy follows. The apparatus is safeguarded by entwined sovereignties of capital, law, and identity. An assault on its logic is framed as hostility toward innovation, national primacy, or personal agency. Regulatory gestures are either pre-empted by lobbying choreography or recast as compliance regimes that further entrench incumbents. Reformist optimism functions as ideological airlock, admitting discontent only after oxygen has been removed. Within this schema, systemic alteration is metabolised as feature request; the source code of enclosure remains read-only.
What endures is the discipline of navigation. Individuals can still engineer micro-escapes (geographic arbitrage, niche cooperatives, artisanal protocol experiments) but these are sub-scale exceptions; they resemble ballast tanks in a sealed submarine: useful for local trim, irrelevant to course. Advising mass adoption of such strategies would be a category error. This essay is not an elegy for an Edenic web. It is an autopsy of a brief developmental phase during which labor, aligned with open standards and plural capital, could have institutionalised a commons. That phase ended; the body was interred; the machinery that killed it still hums today. To insist on hope is to misdiagnose the patient and mislead the living. Accurate mourning is the final act of fidelity to fact.
The internet was buried alive. We heard it scream.
Pocket internets still flicker at the margins. A co-op in Vermont hosts a federated calendar that never sold an ad; hobbyists in Nairobi mirror public-domain ephemera on solar servers the size of a lunch box. Their scale is trivial, their legality contingent, and their uptime measured in heroic afternoons. Yet each node proves the substrate is still programmable by citizens, at least until policy or packet inspection turns hostile. They are not a remedy, only evidence that the corpse twitches where jurisdiction, attention, and capital have not yet converged.